Table of Contents
Junos NAT Configuration Examples
Table of Contents
Junos NAT
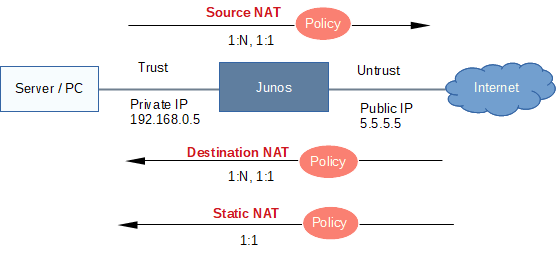
| Source NAT | |
| Destination NAT | |
| Static NAT | 1:1 |
Show
| Operation | Command |
|---|---|
| # show security nat # show security nat | display set |
|
| show source nat | > show security nat source rule all > show security nat source pool all > show security nat source summary |
| show Static NAT (1:1) | > show security nat static rule all # run show security nat static rule all |
| show destination nat | > show security nat destination rule all > show security nat destination pool all > show security nat destination summary |
| Persistent NAT | > show security nat source persistent-nat-table summary > show security nat source persistent-nat-table all |
| > show security alg dns doctoring # run show security alg status |
|
| Disabling DNS and DDNS Doctoring | # set security alg dns doctoring none |
| > show security flow session > show security flow session | no-more |
Configuration
Source NAT(1:N)
Server/Office –> Internet
Interface-based source NAT
set security nat source rule-set 1 from zone trust set security nat source rule-set 1 to zone untrust set security nat source rule-set 1 rule 1A match source-address 0.0.0.0/0 set security nat source rule-set 1 rule 1A then source-nat interface
Pool-based source NAT
set security nat source pool src_nat_pool_napt address 100.100.110.20/32 to 100.100.100.29/32 set security nat source rule-set src_nat_napt from zone trust set security nat source rule-set src_nat_napt to zone untrust set security nat source rule-set src_nat_napt rule napt_1 match source-address 192.168.1.0/24 set security nat source rule-set src_nat_napt rule napt_1 then source-nat pool src_nat_pool_napt set security nat proxy-arp interface ge-0/0/0.0 address 100.100.100.20/32 to 100.100.100.29/32
set security nat source pool src_nat_pool_napt address 100.100.110.20/32 to 100.100.100.29/32 set security nat source rule-set src_nat_napt rule snat_1 match source-address 192.168.10.5/32 set security nat source rule-set src_nat_napt rule snat_1 match source-address 192.168.11.5/32 set security nat source rule-set src_nat_napt rule snat_1 match destination-address 0.0.0.0/0 set security nat source rule-set src_nat_napt rule snat_1 then source-nat pool snat_pool_1 set security nat proxy-arp interface ge-0/0/0.0 address 100.100.100.20/32 to 100.100.100.29/32
Staic NAT(1:1)
Internet –> Server
set security nat static rule-set untrust_to_trust rule RULE-NAME1 match destination-address 203.xx.xx.xx/32 set security nat static rule-set untrust_to_trust rule RULE-NAME1 then static-nat prefix 192.168.0.10/32 set security nat proxy-arp interface vlan.XXX address 203.xx.xx.xx/32
Destination NAT
Internet –> Server/Office
1:1
Destination: 10.1.1.5 → 100.0.0.1
set security nat destination pool SVR_A address 10.1.1.5/32 set security nat destination rule-set 1 from zone untrust set security nat destination rule-set 1 rule 1A match destination-address 100.0.0.1/32 set security nat destination rule-set 1 rule 1A then destination-nat pool SVR_A
1:N
Destination : 1.1.0.1:80 → 10.1.1.5:80
Destination : 1.1.0.1:8080 → 10.1.1.6:80
set security nat destination pool SVR_A address 10.1.1.5/32 port 80 set security nat destination pool SVR_B address 10.1.1.6/32 port 80 set security nat destination rule-set 1 from zone untrust set security nat destination rule-set 1 rule 1A match destination-address 1.1.0.1/32 set security nat destination rule-set 1 rule 1A match destination-port 80 set security nat destination rule-set 1 rule 1A then destination-nat pool SVR_A set security nat destination rule-set 1 rule 1B match destination-address 1.1.0.1/32 set security nat destination rule-set 1 rule 1B match destination-port 8080 set security nat destination rule-set 1 rule 1B then destination-nat pool SVR_B
Juniper Junos CLI Commands(SRX/QFX/EX)
- Junos Basic Setting
- Junos Basic Operation Commands
- How to Configure SRX Chassis Cluster(HA)
- Junos Configuration Command Examples
- Junos Hardware Commands
- Junos Interface Configuration Examples
- How to configure IPSec VPN in Junos
- Junos Link Aggregation Configuration Examples
- Junos Logging Configuration Examples
- Junos Mac address Commands
- How to configure Multicast in Junos
- Junos NAT Configuration Examples
- Junos Policy Configuration Examples
- Junos QoS Examples
- Junos Static Routing Configuration Examples
- How to monitor traffic on Junos SRX (like tcpdump on Linux)
- Junos VLAN Configuration Examples